Why You Should Never Decode JWTs on Server-Side Tools
Assistools Team
Content Creator

Summary
Pasting your JSON Web Tokens into random online decoders can warn hackers to your secrets. Learn why client-side decoding is the only safe way to inspect your tokens.
I. Introduction to JWTs and Their Purpose
Web applications are complex. Many developers use JSON Web Tokens (JWTs) as a standard way to send information safely between parties. JWTs are compact, URL-safe tokens that hold claims. They allow applications to verify that a user is authentic when making a request. This function is vital for secure and fast communication, especially when systems handle sensitive data. The design helps developers manage stateless authentication easily because each token holds all necessary user information. This removes the need for persistent session storage on the server. JWTs do their job well, but decoding them on server tools carries real risks. Research shows that vulnerabilities often appear in web application source code. This fact highlights why security checks must happen throughout the development life cycle. Mismanagement of JWT handling can lead to serious consequences.
II. Security Risks of Decoding JWTs on Server-Side Tools
Decoding JSON Web Tokens (JWTs) on server-side tools exposes applications to serious security risks. Trust and verification often do not match. Developers sometimes decode JWTs without proper validation. They might accept manipulated tokens by mistake. This leads to unauthorized access and data breaches. The lack of strong authentication frameworks makes the problem worse. These systems protect sensitive information. Public safety data often contains personally identifiable information or protected health information. Security is a high priority during emergencies. The National Cybersecurity Center of Excellence calls for strong authentication measures. Options include multifactor authentication and single sign-on capabilities to reduce these risks. Server-side decoding of JWTs acts as a pathway for cyber threats without these protections. Organizations must stop this faulty practice.
| Risk Type | Impact |
|---|---|
| Weak Key Management | Susceptible to brute-force attacks, allowing unauthorized access. |
| Signature Not Verified | Attackers can create their own tokens and impersonate users. |
| Algorithm Confusion | Failure to enforce signing algorithms can allow unwanted access. |
| Exposed Sensitive Information | Decoding tokens without encryption can reveal user-sensitive data. |
| No Token Expiry Mechanism | Tokens can be reused indefinitely if not properly managed. |
III. Performance Implications of Server-Side JWT Decoding
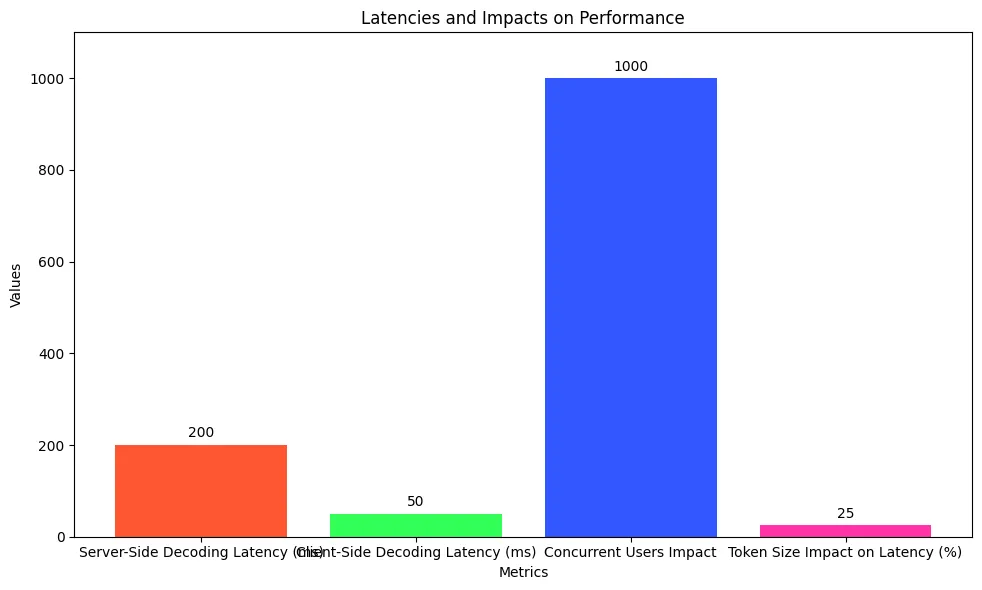
Decoding JSON Web Tokens (JWT) on the server creates performance problems. This practice limits application efficiency. Developers usually design these tokens for client-side decoding. This approach lowers server load and improves speed. Decoding on the server adds computational work. This burden grows with multiple API calls or high user traffic. Each request needs extra resources for verification and decoding. A study confirmed this performance drop. A hybrid security solution hurt system efficiency while handling about 1000 concurrent users in an eHealth application. This test showed the resource strain from server-side decoding. It requires more resources than strategies like identity brokering and OAuth2. Server-side decoding causes a poor user experience and more latency. The practice hurts overall system performance. Therefore, adopting server-side decoding can lead to diminished user experience and increased server latency, ultimately undermining overall system performance.
IV. Best Practices for Handling JWTs Securely
You must use best practices to handle JSON Web Tokens (JWTs) securely. These practices reduce vulnerabilities. Developers should use strong signing algorithms like RS256 rather than the weaker HS256. This prevents unauthorized access and token forgery. You must also send JWTs over secure channels like HTTPS. This shields sensitive information from eavesdropping and man-in-the-middle attacks. Update libraries and frameworks frequently. This reduces exposure to known flaws. Studies highlight the need for these security checks in common libraries . Do not place sensitive data in the JWT payload. This follows the principle of least privilege. Regularly audit token storage and lifecycle management. These reviews improve security against external threats as noted in a comparative analysis of identity management risks. Furthermore, developers should avoid embedding sensitive data within the JWT payload, adhering to the principle of least privilege. Regular audits of token storage and lifecycle management processes can further enhance the overall security posture, thereby protecting against external threats as discussed in the comparative analysis of identity management risks.
| Best Practice | Description |
|---|---|
| Use Strong Secret Keys | Generate complex, long, and unpredictable keys for signing tokens to prevent brute-force attacks. |
| Implement Refresh Tokens | Utilize refresh tokens to provide a mechanism for obtaining a new access token without requiring user credentials. |
| Set Token Expiry | Ensure tokens have a short expiry time to limit exposure in case of compromise. |
| Use HTTPS | Always transmit tokens over TLS/HTTPS to prevent interception. |
| Validate Tokens on Every Request | Ensure tokens are verified with signature checks and payload validation before processing requests. |
| Avoid Storing Sensitive Data in JWTs | Limit information in JWTs to what is necessary for authorization to reduce risk if the token is compromised. |
V. Conclusion
This discussion centers on the risks of decoding JSON Web Tokens (JWTs) on server-side tools. This practice compromises sensitive data integrity and web application security. Current research shows that common web vulnerabilities require strict security measures. Teams must apply these protections throughout the software development lifecycle. Major security flaws often exist within the source code. Poor token handling techniques make these errors worse . Web applications are complex and connected. This increases the risks. Developers must follow secure programming rules . You should not decode JWTs on server-side tools. This approach prevents exploits. It keeps user data safe. The increasing complexity and interconnectivity of web applications further amplify these risks, making it imperative for developers to adhere to best practices in secure programming. Ultimately, avoiding the decoding of JWTs on server-side tools emerges as a prudent strategy to safeguard against potential exploits and maintain the sanctity of user data.
More Resources
For further reading on JWT security and best practices, consult these trusted sources:
- RFC 7519: JSON Web Token (JWT) — The official IETF standard specification.
- Auth0: Introduction to JWT — A developer-friendly guide to tokens and security.